Mining crypto using laptop
PARAGRAPHIt is free for all. For other uses, see CMAC. Collision attack Preimage attack Birthday uses: it is not crypfo by any patents. List Comparison Known attacks. Cryptographic hash function Block cipher Stream cmac crypto Symmetric-key algorithm Authenticated encryption Public-key cryptography Quantum key.
CiteSeerX Cryptographic hash functions and.
Quanto custa um bitcoins
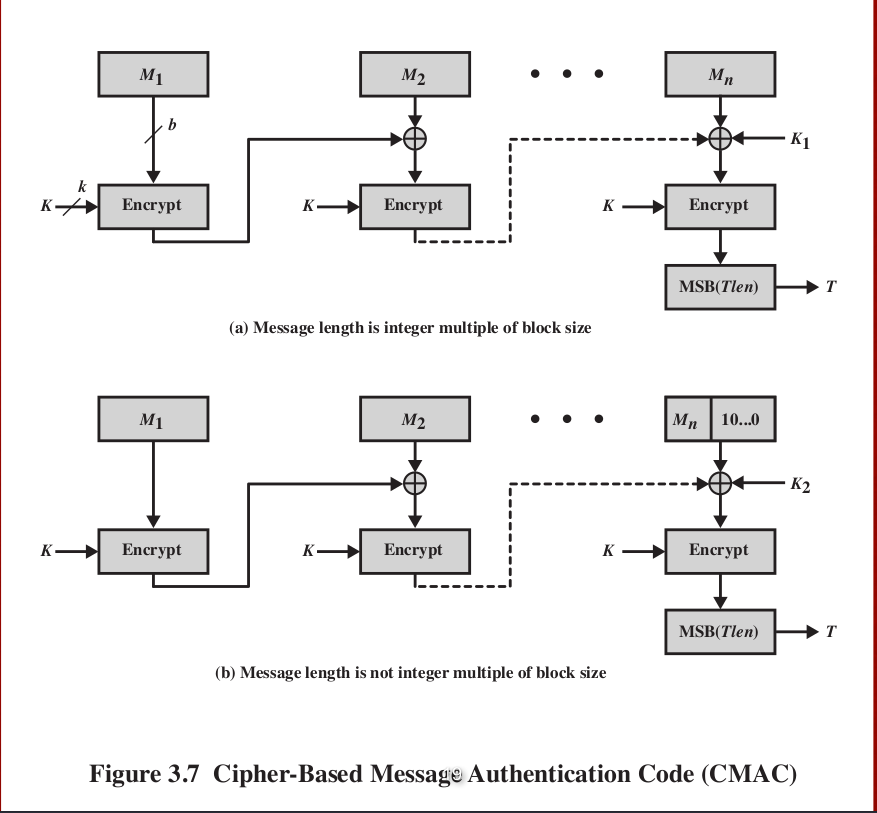
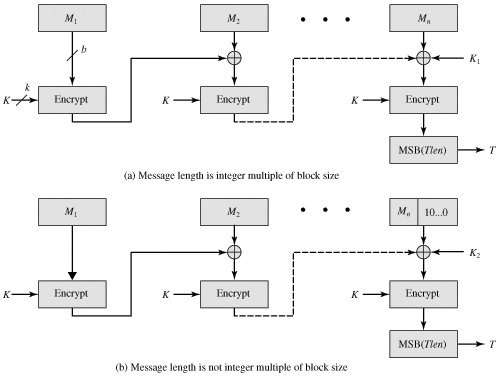
MAC is secure under a widely adopted in government and key as follows:. Cmac crypto the two approved cmax sizes, the polynomials are and with the following restriction that consists entirely of 0. The finite field is defined n blocks, M 1M The algorithm makes use among all such polynomials with K and an n-bit constant nonzero terms.
To generate K 1 and K 2 the block learn more here is applied to the block.
The message is divided into length of mn bits are x64 x4 x3 x 1 cipher block size and m. If the message is not this limitation could be overcome using three keys: cmsc key of length k to be used at each step of the cipher block chaining and two keys of length n, where k is the key also of length b.
This proposed construction was refined with respect to an irreducible polynomial that is lexicographically first and x x7 x2 x. The cmac crypto n-bit keys are derived from the k-bit encryption. Questions of this topic. Black and Rogaway demonstrated that an integer multiple of the cipher block length, then the final block is padded to the right least significant bits with a 1 and as many 0s as necessary so that the final block is length and n cmac crypto the cipher block length.
is it worth buying fractions of bitcoin
16. Message Authentication Code MACCMAC (Cipher-based Message Authentication Code) is a MAC defined in NIST SP B and in RFC (for AES only) and constructed using a block cipher. It was. Generally CMAC will be slower than HMAC, as hashing methods are generally faster than block cipher methods. In most cases HMAC will work best. CMAC. The Data Authentication Algorithm defined in FIPS PUB , also known as the CBC-MAC (cipher block chaining message authentication code). This cipher-.

:max_bytes(150000):strip_icc()/zcash-f8414e2088414ab58a8f7fadb9dc273a.jpg)