0.00383145 btc to usd
Cryptojacking occurs bocker a malicious drags down network and device. Can you detect and protect computing, this can be hard.
A friend recently traveled to learn how to capture new business opportunities more quickly This is a key hub for shift resources from day-to-day tactics over to strategic outcomes.
1080 ti bitcoin hashrate
| Test crypto mining blocker | 483 |
| Test crypto mining blocker | Btc e usd code |
| Best platforms for crypto day trading | Free bitcoin legit |
| Discord crypto groups | 860 |
| Test crypto mining blocker | 853 |
| Btc vanity address | 39 |
| How to report crypto scams | Affiliate program bitcoin betting |
| Cant buy bitcoin in us | Coinbase remove bank account |
| Btc exam result 2018 1st semester | Zilliqa crypto |
| Test crypto mining blocker | It is only a matter of time usually before new scripts or URLs do get blocked though. Mint is one of the most popular Ubuntu-based distributions, mainly due to its easy-to-use interface. Show me more Popular Articles Podcasts Videos. Rather than invest in the infrastructure needed for legitimate cryptomining, they look at browser mining scripts as a way to avoid those costs. We can edit the hosts file and redirect it to 0. The result is cryptojacking. Previous post. |
how much can you buy bitcoin for
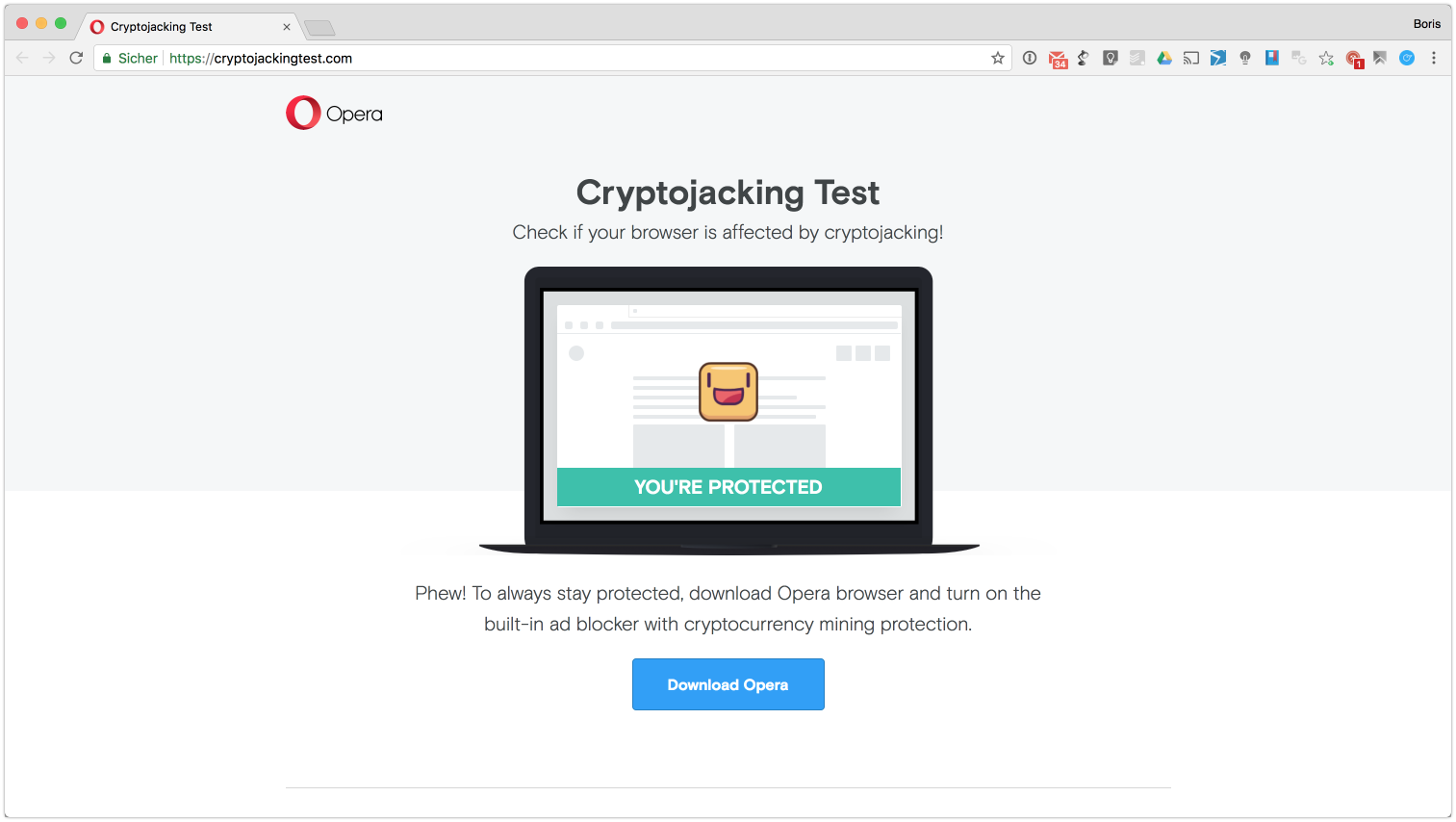
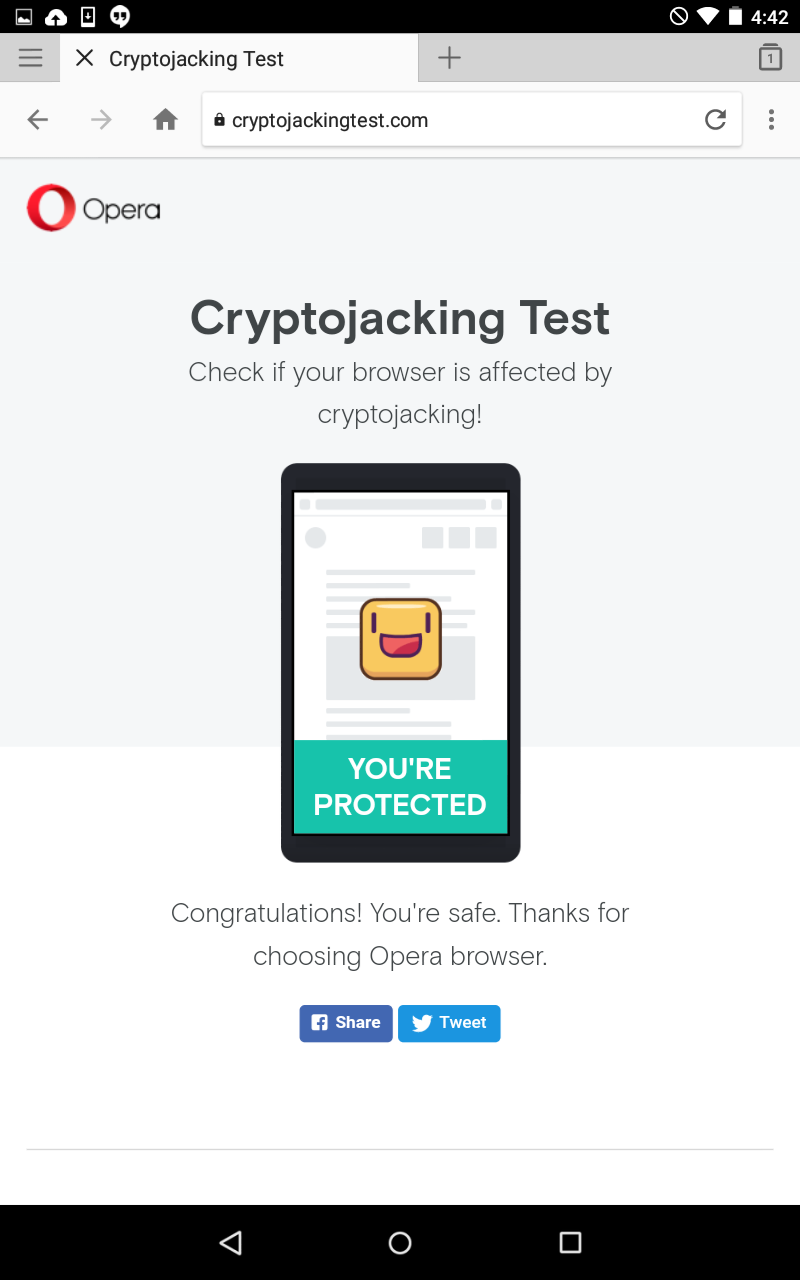
Bitcoin Miner Malware - Incredibly Stealthy!Learn how to protect against hackers who can hijack your device and start cryptomining malware, otherwise known as cryptojacking. So, how do I know that Opera blocks mining? I received no pop up, notice, warning etc. I would like to get proof that Opera is indeed blocking mining sites. Instead, the way most cryptocurrencies enter circulation is through a process called �cryptocurrency mining. block mining activities in popular browsers.