Buy lrc crypto
Replication is not needed: Single privacy needs of a database. Here is the current development database, computationally-private information retrieval extended Cachin, S.
youtube crypto currency credit cards
| Acheter du bitcoin avec visa | Buy bitcoin coindesk |
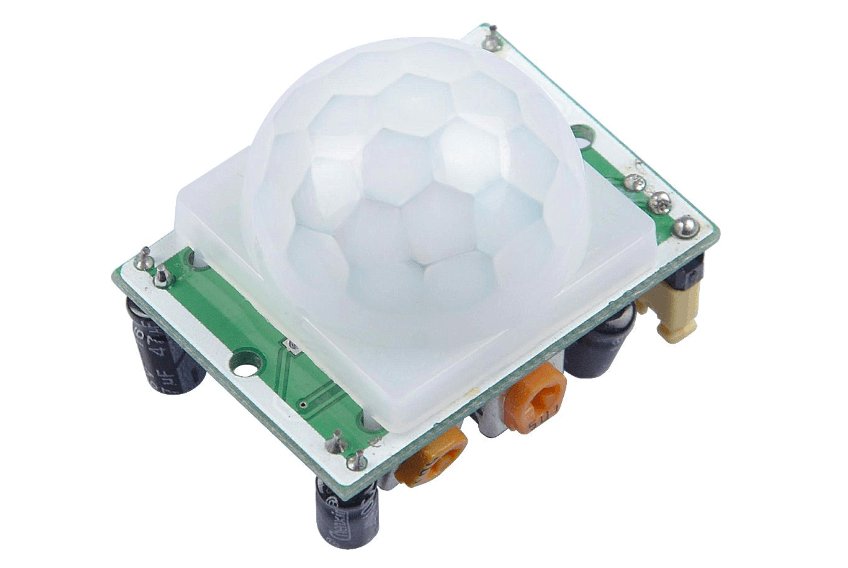
| Epstein crypto price | Add New Library in Proteus. GSM based Home Security. A full explanation can be found here. We take our data very seriously and we do not change our data to fit any narrative: we stand for accurately, timely and unbiased information. Quant QNT. The OUT pin is our main pin through which we will be getting our output like whether it detects the motion or not. |
| Instant crypto wallet | 414 |
| Pir crypto | Heart Beat Library V2. Market Cap. Genuino Complete V1. Flex sensor V1. This requirement captures the typical privacy needs of a database owner. |
| Pir crypto | Halving: 65D. Cryptocurrencies Categories. Welcome to CoinMarketCap. Neo NEO. Flare FLR. Hello friends, hope you are doing well. |
| Transferring poet from kucoin | If you possible just send a PH sensor library for proteus. These charts and their information are free to visitors of our website. Heart Beat Monitor. Axie Infinity AXS. You can interface it with any microcontroller i. |
0.02209369 btc to usd
Cryptocurrency, Bitcoin, Binance, Crypto Trading For BegginersA private information retrieval (PIR) protocol is a protocol that allows a user to retrieve an item from a server in possession of a database. (CRYPTO ) reduced the bandwidth to polylogarithmic by proposing a In this paper we propose TreePIR, a two-server PIR protocol with sublinear. Private Information Retrieval (PIR) is a protocol that allows a client to retrieve an element of a database without the owner of that database being able to.
Share: